4 minutes
Identify the key members of your credit union’s incident response team before a data breach.
In the cybersecurity world, 2018 closed with a bang in the form of two “mega breach” notifications. Marriott announced the compromise of up to 500 million customers while Quora’s data breach affected up to 300 million. Statistics point to a continued rise in the number of cyber attacks, and though prevention techniques and proper cyber hygiene can reduce risk, a credit union must be prepared to respond to a data breach. To that end, Tech Time and LEO Cyber Security, CUES’ strategic partner for IT and cybersecurity, are pleased to present a series of articles on the subject of cyber crisis management.
In the September “Tech Time” column, author Jim Benlein stressed the importance of credit unions having an incident response program. Going forward, this series will introduce best practices and present guidance for putting in place a cyber crisis management program that fits your credit union.
In this article, we consider the incident response team.
The hypothetical presented in the September article postulated a call from Special Agent Joe Gannon informing a credit union vice president that the FBI found credit union member information on the dark web. Who should be at the table during the initial discussions of this incident?
The obvious first choice would be the department most able to confirm the existence and scope of a security incident, namely the information security (“infosec”) office. (Not all credit unions have dedicated infosec personnel on staff; some use cybersecurity professional service companies to provide those resources.) But the response to a cyber incident should not live entirely within the infosec group. A representative from your organization’s legal department or your outside counsel should also be at the table. Your legal team can help you determine whether the incident triggers state data breach notification laws, plus preserve evidence and assist with any cybersecurity claims. And, since attorney-client privilege only applies to communications between client and attorney for the purpose of obtaining legal counsel/guidance, your lawyer(s) should be directly involved in discussions to protect their knowledge of the incident in the event of post-breach litigation.
If, in our hypothetical, the FBI is aware of leaked information, the news may also be made public, which is why your credit union’s public relations/communications department should be part of the cyber crisis management team. PR assists in drafting breach notification letters; composing statements to the public, press and individuals whose data has been compromised; and coaching executives prior to a public interview.
If a credit union employee was involved in the data breach, either as a data subject or as a suspect, a representative from human resources should be part of the team. HR assists in interviewing employees involved in the breach, communicating with employees about the breach and preserving evidence associated with credit union employees. (Keep in mind that an employee involved in the breach may be just as much a victim as the credit union and its members, such as in the case of an attack through a phishing email sent to employees.)
Cyber crisis management teams may also benefit from designating a team member, such as corporate security, as the law enforcement liaison. This team member also assists when the cyber incident stems from physical access to the credit union or where a device is lost or stolen.
Last in our discussion of core team members, but certainly not least, is the incident response director. This person focuses on the big picture, assigns and monitors team tasks, serves as the main point of contact with executives and board members, and generally directs the team through the process. Though this individual can be a member of any of the above-mentioned disciplines, it is recommended that the director wear only one hat—that of leading the incident team—during a response.
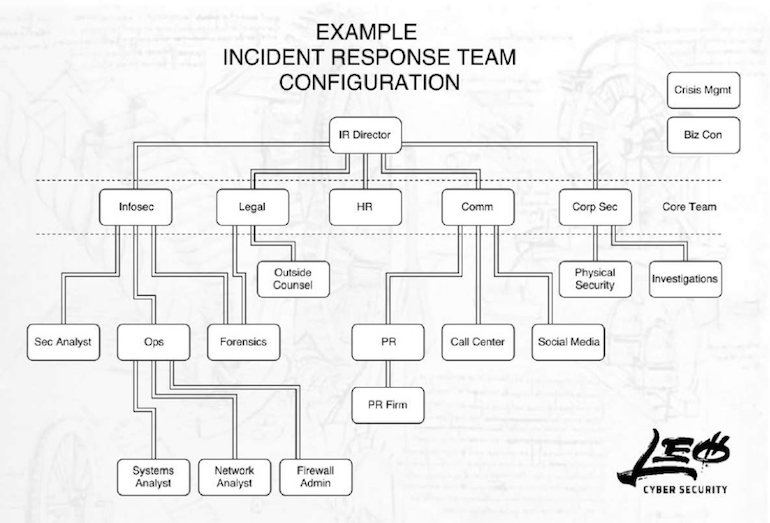
The above figure represents an organizational example of an enterprise-wide cyber crisis management team. The core team members interact with the director and each other, while support members percolate information up to the core team members and accept tasks from the core team. This organizational structure facilitates effective and efficient communication and coordination.
However your credit union decides to organize its cyber crisis management team, consider identifying those members before a problem presents itself. Review the incident response plan with your team members and conduct a tabletop exercise/simulation at least annually.
Seth Jaffe, CBCP, JD, is official rocket scientist in residence for CUES strategic partner LEO Cyber Security, Dallas. Hailing from NASA’s Mission Control Center, he brings a unique perspective to incident response, applying aspects of one of the world’s preeminent emergency operations platforms to cyber response. In addition to 20-plus years of technical experience, Jaffe was previously a member of the data protection task force at a large law firm and served as the lead legal team member of an incident response team at a major U.S. airline. He is a certified business continuity professional and holds a juris doctorate, which is why he also wears the general counsel hat at LEO.